Hi,
I have a question about a HTPP connection with CSRF token handling in Celigo when posting to a SAP endpoint.
The setup is as follows: I need to do a POST to SAP using Basic Auth. Before that, I perform a GET (also with basic auth) with the header x-csrf-token: Fetch, which returns a token in the response. That token then needs to be included in the POST request header as x-csrf-token.
This works fine in Postman.
However, in Celigo, it doesn’t work as expected. I tried doing a GET to fetch the token and then using that token in the POST step, but it still fails. I noticed that SAP returns a different token depending on the IP address making the request, so I’m wondering if the GET and POST are being executed from different IPs in Celigo, causing the token to become invalid.
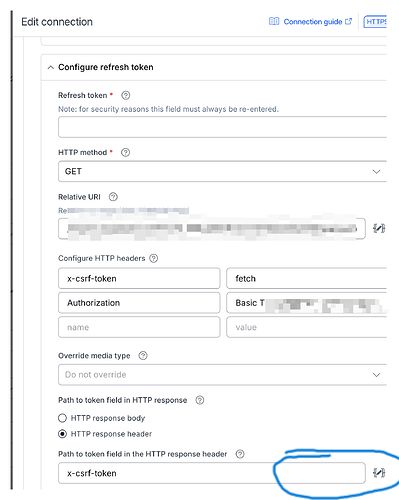
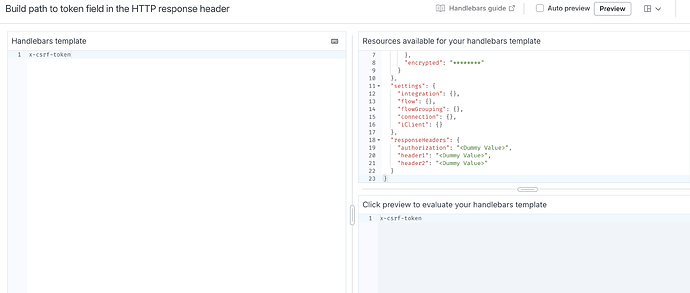
I also tried manually adding the x-csrf-token in the flow headers and setting up a connection using custom auth, where I filled in both the Basic Auth header and the token inside the http headers:
No success. Even hardcoding the token didn’t work — possibly because it’s bound to a different IP/session.
I even tried triggering a failed call to force a token refresh, but that didn’t resolve it.
I also tried using the connection Basic Auth and filling in the token manually but this also doesnt work.
So in postman its:
Get > Receive token in header
Use that token in the POST
Success
In Celigo
Get > Receive token in header
Use that token in the POST
Fail
Hope someone can help